Building an Extensive Homelab Environment
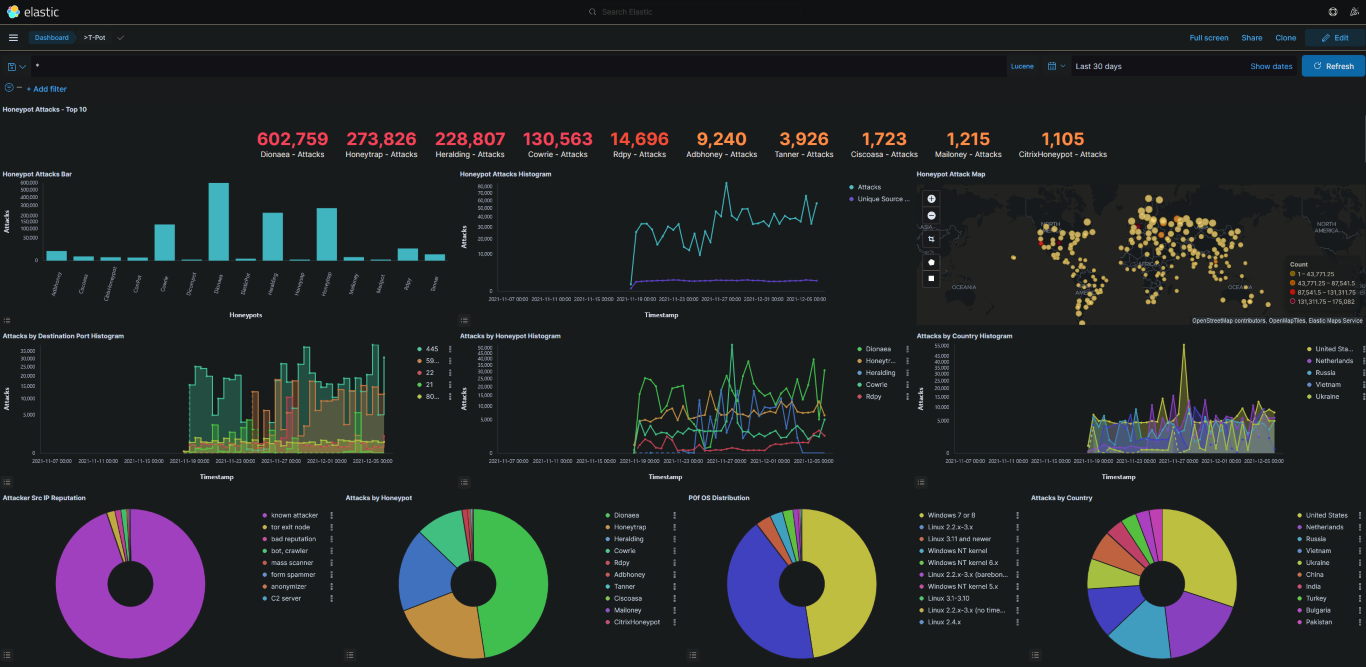
Over my time studying networking and cybersecurity and my free time as a recent graduate, I have built a large homelab environment. My envvironment includes a full, virtualized Active Directory domain running DNS/DHCP in it's own VLAN and full monitoring with PRTG. I have many dockerized applications running accross multiple servers, some of which run on a kuberenetes cluster based on Portainer. I run many VMs in a proxmox cluster, but have used ESXi and Hyper-V for running VMs in the past. Some of my VMs include a Pterodactyl game server, Security Onion, AWX (upstream/open source Ansible Tower), OpenWRT, and Portainer as mentioned earlier.
I list this as an ongiong accomplishment as a good Homelab is never complete and requires ongoing maintenance and upgrades!